Types of IPv6 addresses
By default your IPv6 enabled devices will use an IPv6 address that can be reached by anyone from the outside (even from the internet). You might ask, what about private addresses? Actually there is nothing like a private address in the world of IPv4. Something similar is available, but it’s called differently. Let’s start from the beginning:
From a high level view an IPv6 address is made of two parts:
-> Prefix
-> Suffix – Interface identifier
Let’s take a look at just a few different types of IPv6 addresses:
Link-local (prefix FE80::)
If you run ipconfig / ifconfig on your device you’ll see an IPv6 address that starts with prefix FE80::
This is a constant address which is immediately and automatically available and can be used for communication inside your LAN, across switches but not across routers, to other Link-local addresses. Link-local addresses in IPv6 exist on each interface, regardless of whether the interface has an address assigned from DHCP or is configured using another method.
The prefix FE80:: is always the same and followed by the suffix (aka interface identifier). Latter is generated automatically (usually based on MAC address).
Unique Local Addresses – ULA (prefix FCxx: to FD:xx)
Equivalent to reserved private addresses in an IPv4 network (like 192.168. or 172.16) , that start with FCxx: up to FDxx: and cannot be routed to the internet. They are routable only within the scope of such private networks, but not in the global IPv6 internet. In a private home network you won’t need ULAs.
Global Unicast (prefix from ISP)
Equivalent to public IPv4 addresses but no longer limited to a router. Instead every device in your local network can be assigned a global address that is routable. When your home router makes a DHCPv6 request to your ISP, it will get assigned with the global unicast prefix. See “automatic Stateful Address Autoconfiguration” below.
Obtaining an IPv6 address
A local device can obtain its IPv6 address via three different ways:
-> automatic Stateless Address Autoconfiguration (aka SLAAC)
-> automatic Stateful Address Autoconfiguration (via DHCPv6 server, similar to IPv4 DHCP server)
-> manual configuration
SLAAC
In a nutshell SLAAC (auto configuration without a DHCP server) is always used for link-local addresses and in home environments usually the default for global unicast addresses.
First, the client discovers the local router using the Neighbor Discovery Protocol (NDP), sending a Router Solicitation message (a special ICMPv6 packet type). The router itself will answer with a Router Advertisement (RA) message.
The network prefix provided by your ISP combined with the ‘interface identifier’ part will generate the Global Unicast address via SLAAC. Connected to the same ISP this address will (should) never change.
Btw: The RA message will be sent periodically even without a request. It can include several network configuration information. For example, the client can be told to obtain a Unique Local Address (M Flag) from a DHVPv6 server. Additionally clients can be informed to obtain other configuration information like IPv6 DNS Server (O Flag) via an additional DHCPv6 server.
Recommendation for home networks:
I’ve configured my local router to send the O flag (and connect via DHCPv6) and omit the M flag. This way all IPv6 clients will have assigned a Link-local address and a Global Unicast address. My local DHCPv6 server informs clients about where to find the (pi-hole) IPv6 DNS server.
Privacy Extensions
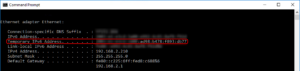
Someone can now assume that a specific device will always communicate from the same source ip address (in case the ISP hasn’t changed). This is only true as long “Privacy Extensions” hasn’t been enabled. All modern operating systems have Privacy Extensions enabled by default and as such you’ll end up with IPv6 address whose ‘interface identifier’ is not based on the mac address (but a random hash). Windows 10 for example will show the real and fake address if you run ipconfig. The ‘temporary address’ is used for outgoing connections until the next reboot. You definitely want to disable this for server applications (like FTP) or at least using a DNS name.
Linux – Disable Privacy Exentions
In order to disable privacy exentions under Linux, execute the following commands and reboot:
cat >> /etc/sysctl.conf <<EOT net.ipv6.conf.all.use_tempaddr=0 net.ipv6.conf.default.use_tempaddr=0 EOT sysctl -p